
When you implement a governance, risk, and compliance (GRC) platform, you’re not just adding another piece of software. You’re centralizing the most sensitive parts of your business: security controls, vulnerabilities, audit evidence, risk registers, vendor data, and remediation plans.
Think of it as handing over the keys to your kingdom — or the Rosetta Stone to your entire technology stack. If that platform is compromised, the fallout doesn’t just hit the platform provider. It hits every customer whose sensitive data was stored inside.
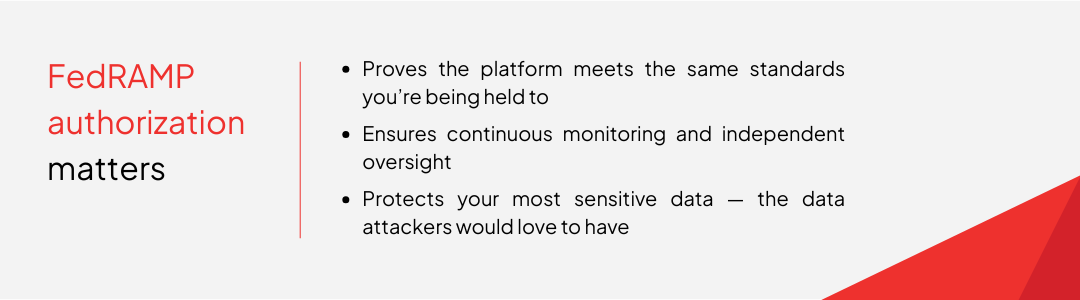
That’s why FedRAMP authorization matters.
Attackers know that GRC platforms contain:
In other words, everything an attacker would need to exploit your environment at scale. A breach here isn’t just data leakage. It’s a blueprint for how to attack your systems.
Unfortunately, there have already been examples of platforms in the compliance and audit space experiencing major breaches and data co-mingling issues. Those incidents highlight the obvious question: why would you entrust that level of information to a platform that doesn’t meet the same standards you’re expected to meet.
FedRAMP authorization isn’t just a rubber stamp. It demonstrates that a platform has:
For customers, that means the platform isn’t just claiming to be secure — it has to prove it, every month, through continuous monitoring and oversight by the FedRAMP Program Management Office and sponsoring agencies.
Imagine a contractor that uses a non-FedRAMP GRC platform. That platform suffers a breach, exposing customer data. The attacker now has:
Within days, the contractor’s own systems are compromised using the attacker’s new playbook. The breach isn’t limited to the platform provider — it cascades to every organization whose data was stored there.
That’s the nightmare scenario FedRAMP is designed to prevent.
Some companies assume FedRAMP only matters if you’re working directly with federal agencies. The reality is broader:
In short: if a platform isn’t secure enough for the federal government, why would it be secure enough for your business.
At Diligent, we take this seriously because we know what’s at stake. Our platform is:
That means customers can confidently entrust their most sensitive compliance data to the platform, knowing it’s protected by the same standards the government itself requires.
And because FedRAMP requires continuous monitoring, customers also benefit from the ongoing oversight, reporting, and transparency that comes with it. It’s not just a one-time certification. It’s a continuous commitment to security.
If you’re evaluating GRC platforms, here are the questions to put on the table:
If a vendor can’t answer those questions with clarity and proof, that’s a red flag.
When you put your compliance posture into a platform, you’re betting the business on that provider’s security. Without FedRAMP authorization, that bet comes with unnecessary risk.
In a market where breaches are inevitable and attackers are looking for the easiest way in, FedRAMP authorization isn’t just a badge. It’s a baseline.
For organizations evaluating their options, the question is simple: would you trust your business to anything less?
Explore Diligent's FedRAMP-authorized solutions to protect your organization's critical assets with continuous monitoring, independent validation, and government-grade security.